Q. Do I need to modify my ERP to get PerimeterMFA protection?
Absolutely not!
We create a Perimeter of Protection at the application server level so modifications are never needed to your enterprise application.
Q. Can I use this for applications in a Vendor's Cloud?
Yes! You can utilize our native integration with Active Directory Federation Services.
Q. How long does it take to install the PerimeterMFA System?
You should plan on 30 minutes per application for the full installation and configuration.
Q. What happens if a user forgets their mobile phone? How would they access the system?
The Administration Console allows you generate a temporary TOTP code for any user so they can log in and continue to be productive even without their smart phone.
Q. How do the Biometrics work?
The PerimeterMFA system constantly learns about the unique keyboarding rhythms and cadence of each user as they type in their username.
After a sufficent learning set has been established for a user, subsequent logins are compared to historical data and a confidence score is established.
You can configure the system to bypass secondary MFA challenges if the confidence score is high enough.
Q. Can I set up some users with TOTP and some users with Pattern Unlock?
Yes. You choose a "default" method (TOTP or Pattern), but you can override this at the individual user level.
Q. Can I customize the Phone Call instruction message?
Of course. You can also customize the "Thank you" message at the end of the call.
Q. Do I have to use the Telephony and SMS Messaging features?
No, these are configurable options in the Administration Console.
Q. Can I change the Caller ID?
Yes. We recommend you use a number and Caller ID that is familiar to your users like your Help Desk.
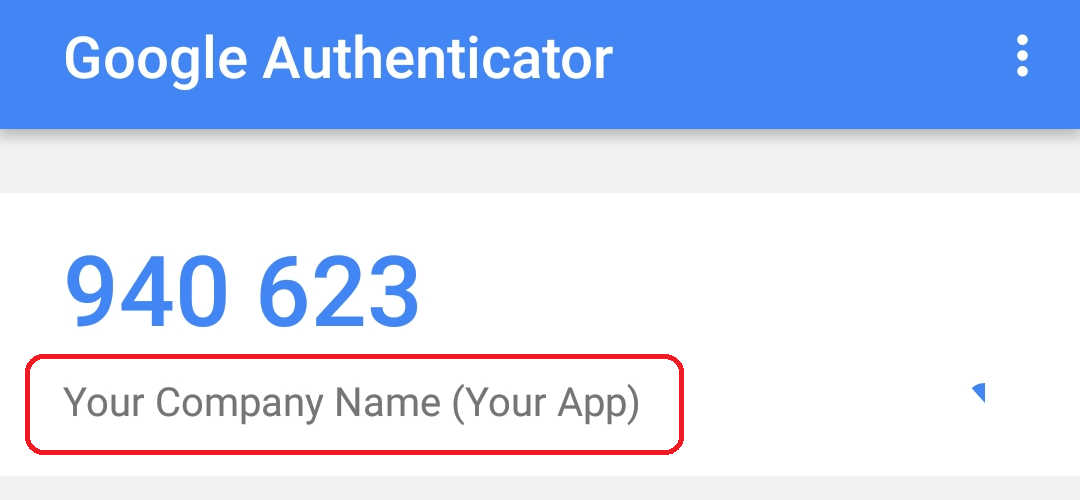
Q. Can I control what information is in the QR Code?
Yes. You determine the Company Name and Application Name in the QR Code that will be displayed in the Authenticator App.
Try it yourself!

Q. Does this integrate with my monitoring or ticketing system?
Yes, there are events that are exposed that can be integrated with just about anything.
Q. Can I turn off PerimeterMFA protection for users inside our main office or using our VPN?
Certainly. Our robust Exemption Management system lets you configure IP patterns (i.e. 10.*.*.* or 192.168.*.*) that will bypass the secondary MFA challenge.
You can also configure exemptions by:
Individual users (i.e. cranky.user@nicecompany.com)
User-Agents (i.e. Python-urllib/*)
URL Patterns (i.e. /images/*;/css/*)
Q. Can I use the PerimeterMFA System with other applications besides my ERP?
Yes. The PerimeterMFA System will protect virtually any application running in a J2EE server such as
IBM WebSphere, Oracle WebLogic, JBoss, Apache Tomcat, Jetty, GlassFish, etc.
You can even choose to share configurations across applications so users only need a single TOTP code to access
all of your protected applications.
Q. What is a user lockout?
After too many consecutive failed attempts to pass the PerimeterMFA challenge, a user will become "locked out" and will
no longer be able to pass the perimeter of protection. This lock out has no impact on the user's access to other
applications as we do not modify the Active Directory or LDAP records, we simply stop the user from accessing the protected application.
The number of failed attempts before lockout is configurable in the Administration Console.
Q. How do I unlock a user?
Unlocking a user is just a click away in the Administration Console - or use the REST API.
Q. What about integration with my in-house systems?
PerimeterMFA provides a comprehensive REST API that allows you to leverage all of the features
and protection for your home-grown applications.
Q. Can we change the look and feel of the PerimeterMFA Screens?
Yes, these are just HTML pages.
Q. What if the user gets a new phone and needs to re-scan their QR code?
You can reset the user in the Administration Console and the next time the user logs in, they will be shown their QR code.
Q. Where does my users' login data go?
PerimeterMFA is a completely self-contained solution. No data ever leaves your premises.
Q. Can we send phishers to a honeypot system?
Yes.
You also have the option to not display the lockout screen so you can continue to
gather forensic information during an unauthorized access attempt.
Q. What about other protocols like RDP, Telnet or SSH?
We support them all!
We deliver native functionality that allows you to protect your Windows servers and all of your *NIX servers.